39 an rfid label on a box is an example of what type of physical security detection method?
US7151455B2 - Activating a data tag by load or ... - Google Patents Mechanically and reversibly activating or deactivating a radio frequency identification (RFID) data tag. An RFID tag includes an RFID chip for storing an RFID code, an antenna for communicating a radio frequency (RF) signal, and a mechanical switch coupling the RFID chip to the antenna. Closing the mechanical switch enables the RFID chip and the antenna to communicate the RFID code via the RF ... What is Physical Security? Measures, Best Practices + PDF Guide Security experts agree that the three most important components of a physical security plan are access control, surveillance, and security testing, which work together to make your space more secure. Access control may start at the outer edge of your security perimeter, which you should establish early in this process.
Radio-frequency identification - Wikipedia RFID tags are used in many industries. For example, an RFID tag attached to an automobile during production can be used to track its progress through the assembly line, RFID-tagged pharmaceuticals can be tracked through warehouses, and implanting RFID microchips in livestock and pets enables positive identification of animals.
An rfid label on a box is an example of what type of physical security detection method?
Ch. 9 Quiz CTS1134 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. How is a posture assessment performed on an organization? A thorough examination of each aspect of the organization's network is performed to determine how it might be compromised. Question28 11pts what type of door access control is - Course Hero key fob lock Question 29 1 / 1 pts An RFID label on a box is an example of what type of physical security detection method? Correct! asset tracking tagging video surveillance via CCTV tamper detection motion detection technology asset tracking tagging US7889084B2 - ID detection device and ID detection method - Google Patents An ID detection device includes a transmit/receive antenna unit having a transmit/receive antenna and a movement mechanism for making the transmit/receive antenna scan, wherein a file folder in which the RFID tags are arranged close to one another in a row is set on the transmit/receive antenna unit, to make the transmit/receive antenna scan in a row direction in which the RFID tags are arranged.
An rfid label on a box is an example of what type of physical security detection method?. Smart garbage monitoring system using sensors with RFID over internet ... 5 CONCLUSION. This paper concl udes that by using this smart garbage monitoring system using RFID over IOT's. we can easily dispose the waste present in the garbage bins as early as possible ... How is a posture assessment performed on an organization a A thorough ... An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging What statement regarding the different versions of the SHA hashing algorithm is accurate? a. US20110099117A1 - Device, system and method for verifying the ... - Google A physical uncloneable function (PUF) pattern is used for verifying a physical condition of an item. The PUF pattern is arranged to be damaged in the event that said item is exposed to a predetermined environmental condition. Verification of the physical condition of the item, is carried out by obtaining a measured response from the PUF pattern, and comparing the measured response with a ... Using RFID for Inventory Management: Pros and Cons - Camcode The use of RFID for inventory management requires a scanner that uses radio waves to communicate with an RFID tag. The tag itself contains a microchip that allows the reader to read data and also write data to the tag for real-time updating in place. Each tag is wrapped in a material like plastic or paper for protection and can be affixed to a ...
What Is RFID Technology and How Can I Use It? - Shopify RFly, for example, created a drone that scans RFID tags and locates products inside a warehouse. If the item is stacked on a high shelf, the drone will collect it. With RFID-enabled drones, the health and safety risks of a factory worker are diminished. There's no need for them to use machinery or climb ladders to retrieve the item. Radio Frequency Identification (RFID) | FDA Active RFID tags are powered by batteries. RFID tags can store a range of information from one serial number to several pages of data. Readers can be mobile so that they can be carried by hand, or... Free Computers Flashcards about Chap 9 and 10 Quiz - StudyStack An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging: What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. Chapter 9 Flashcards by Victor Mendez | Brainscape An RFID label on a box is an example of what type of physical security detection method? Asset tracking tagging 30 What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths Decks in Networking+ Class (22):
Network+ 8th Edition Chapter 9 Flashcards - Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging asset tracking tagging 12. RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database. Security+ Exam Questions Flashcards | Chegg.com B. Protect data in transit from unauthorized disclosure. C. Ensure systems are not susceptible to unauthorized changes. D. Secure data to prevent unauthorized disclosure. 1. C. The administrator should ensure systems are not susceptible to unauthorized changes, an element of integrity. A security program should address the three core security ... Ch9 network Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging. What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. On a Linux based system, what command can you use to create a hash of a file using SHA-256? ...
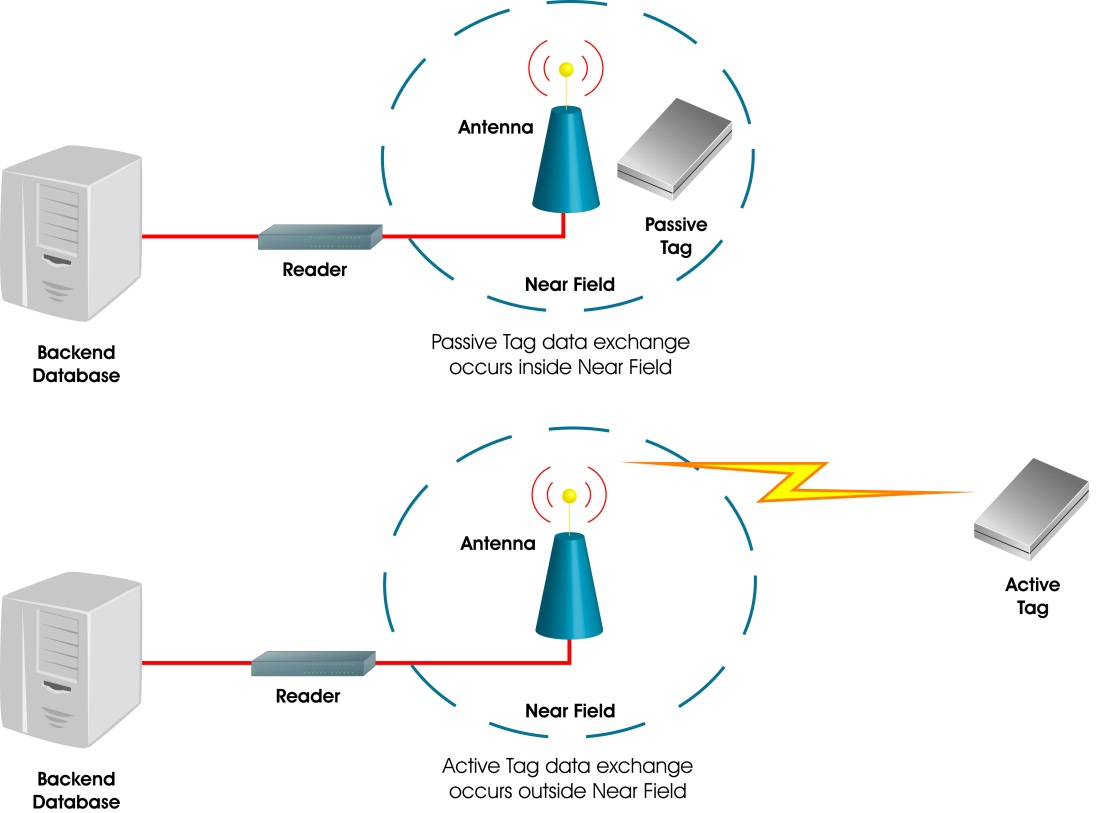
What are RFID Tags? Learn How RFID Tags Work, What They're ... - Camcode RFID tags are a type of tracking system that uses smart barcodes in order to identify items. RFID is short for "radio frequency identification," and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program.
Chapter 9 -- Network II Flashcards & Practice Test | Quizlet A) Polymorphic malware can change its characteristics every time it is transferred to a new system. B) Polymorphic malware is designed to activate on a particular date, remaining harmless until that time. C) Polymorphic malware is software that disguises itself as a legitimate program, or replaces a legitimate program's code with destructive code.
CA2639358A1 - Coupon provided with rfid tag and method of using the ... RFID devices, commonly called RFID tags, are thin transponders (transceivers) that include an integrated circuit chip having RF (radio frequency) circuits, control logic and memory, plus an...
Access Control and Fire Alarm System Integration - Kintronics A software solution is the easiest type of system to implement because only a single wire is required between the fire control box and the closest IP reader. In general, this type of system can be used to open all the doors (in a fire) or close all the doors (emergency lockdown). The diagram above shows a button connected to one of the IP readers.



Post a Comment for "39 an rfid label on a box is an example of what type of physical security detection method?"